Authorisation using VO information
Authorisation using VO information
A Virtual Organisation (VO) represents a research community and, in practice, it is just a group of users. VOs are created to organise a community of researchers, who can share resources across the EGI Federation and other services to achieve a common goal, as part of a scientific collaboration.
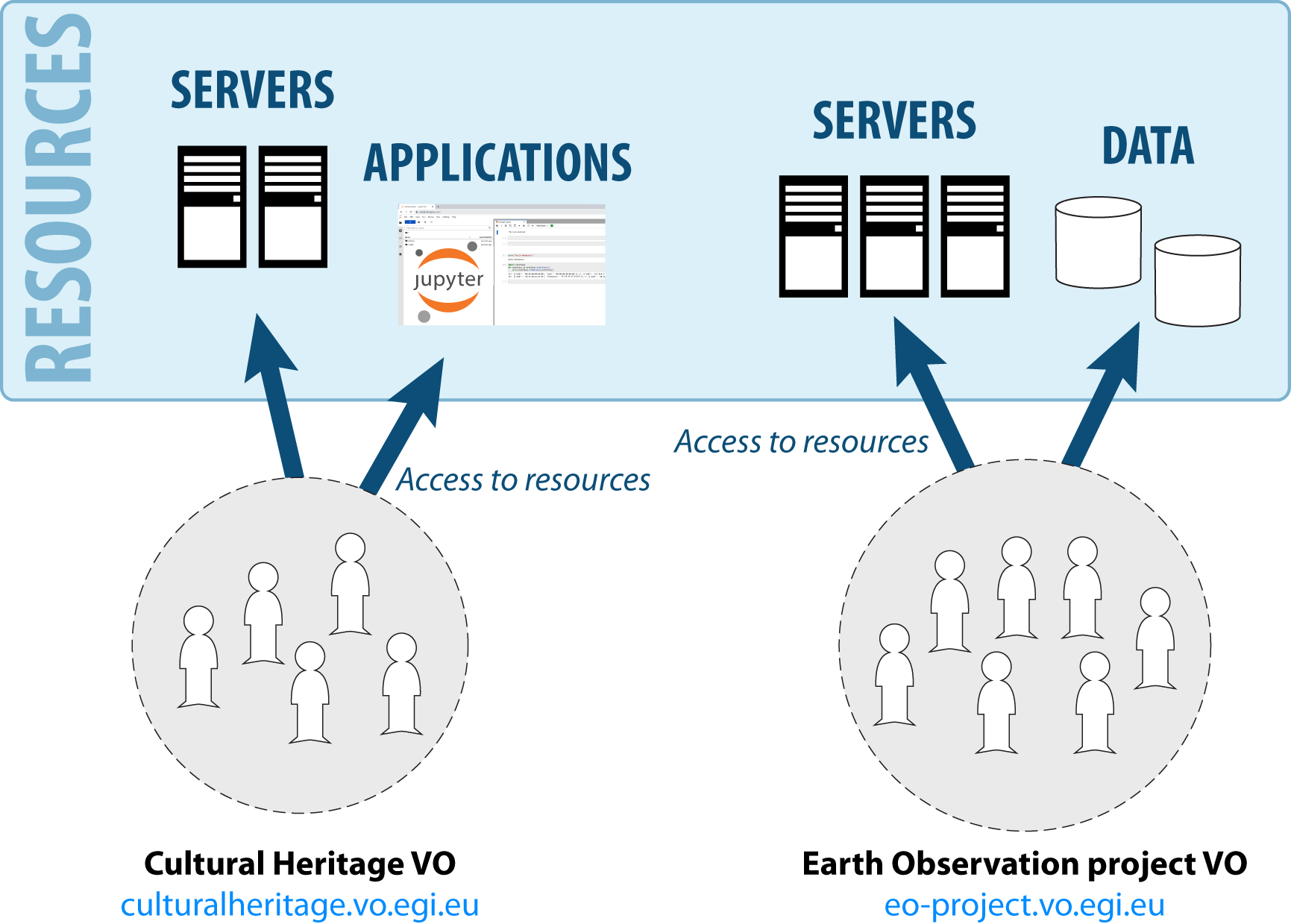
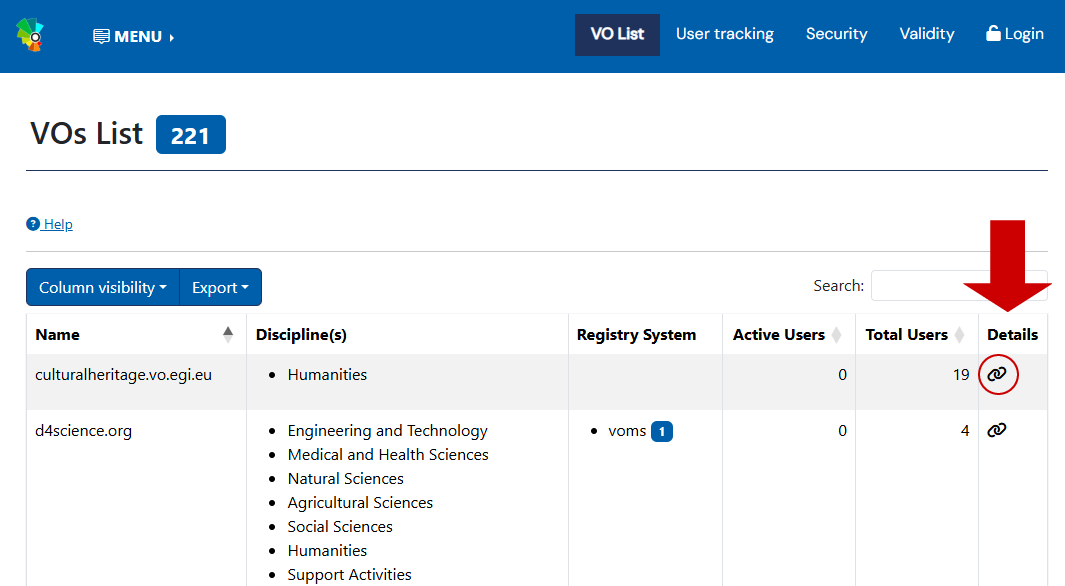
Existing VOs can be found in the EGI Operations Portal.
Click on the icon under the “Details” column to access more detailed information of the VO.
There are different ways to join a VO:
Often, your request to apply for VO membership will be evaluated by a VO Manager before you are accepted in the VO.
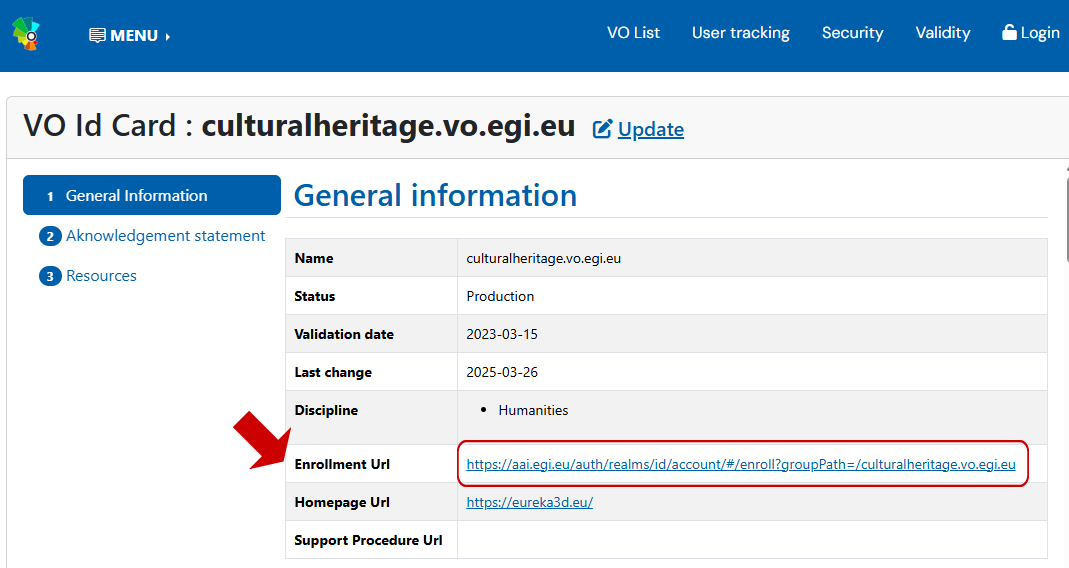
To register a new VO, access the VO registration page of the Operations Portal. You will need to log in via Check-in and fill in the VO ID card, which is the basic information for the VO.
The VO registration process is detailed in the procedure PROC14 VO Registration.
The person registering a VO is considered the administrator of the VO, also known as VO Manager. Additional VO Managers do not need to be included at the time of the VO creation, they can be added later.
A VO is managed by its VO Managers. VOs can have more than one administrator, and they are responsible for the correct operation of the VO. The functions of the VO Managers include:
VOs can be structured in groups, to organise the different permissions that users have inside a community. For example, inside a VO there can be a group for users that will manage cloud infrastructure, another group for users that access a specific application, other group for users that will attend a workshop and need access to Notebooks, etc.
Check-in offers two tools to organise a community:
Follow the links for detailed information on how to manage VO groups.
Authorisation using VO information
Group Management in Check-in via Keycloak
VO management through the EGI Attribute Management service Perun
X.509 / VOMS based authentication and authorisation